DeNexus' mission is to build the Global Standard of Industrial Cyber Risk Quantification for Agencies, Shareholders, Investors, Boards, and the Risk Transfer Market. Our flagship product DeRISK is an evidence-based Cyber Risk Quantification and Management -CRQM- SaaS platform for industrial corporations and (re)insurers of cyber risk powered by AI/ML and Probabilistic Inference. DeRISK provides an inside-out and outside-in view of the risk, at the unit industrial facility and portfolio levels.
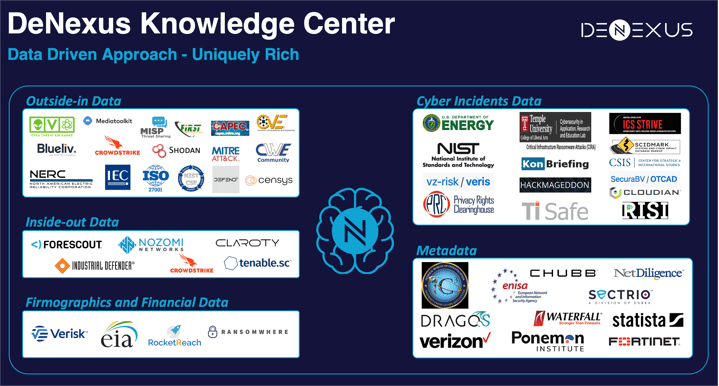
The DeNexus Knowledge Center is where DeRISK data, insights, and intelligence reside. It hosts and leverages the critical asset data from inside the client OT network (Inside-data) together with a global consortium of public, private, and proprietary threat intelligence, cyber-breach, and loss data (Outside-data) to provide industrial stakeholders with the most credible and accurate view of their industrial asset’s cyber risk posture.
 Where data, insights, and intelligence reside
Where data, insights, and intelligence reside
The main hurdles to designing and building systems that quantify cyber risk are (1) the challenges involved in identifying cybersecurity risk factors, and (2) the scarcity of reliable and relevant data for these risk factors.
Some of the difficulties in capturing data on cyber incidents are related to the lack of systematic procedures for storing the relevant data, the partial view of the problem, and privacy. But, at the same time, new sensors and telemetry that monitor systems, and many cyber threat intelligence solutions are available.
Therefore, there is a gap in generating cyber data and relevant, actionable knowledge related to OT/ICS cyber risk. Ultimately, quantifying industrial cyber risk is hard!
Because risk is defined as the probability of a loss event occurring in a given unit of time multiplied by the expected magnitude of loss resulting from that loss event, the needed information – broadly speaking – is about the organization itself (firmographics), the cyber threats (outside-in), the target network, its vulnerabilities and its defenses (inside-out) as well as the technical and financial impact caused by each cyber incident over time! – Cyber Risk is dynamic!
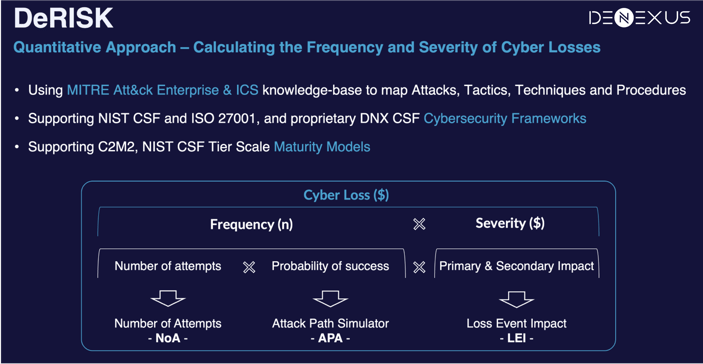
And, since the purpose of CRQM is the management of the cyber risk, another enterprise-level risk, information about the business context, underlying industrial processes, the cost and effectiveness of mitigation projects, and portfolio exposure is also required. In other words, gathering data for a real evidence-based CRQM system is cumbersome. A knowledge base that brings together the data and intelligence created by this effort is a game changer!
At DeNexus we are trending towards having evidence-based inside-data from 10% of the operating assets in the renewable power generation space in the US (a $350 billion industry) and expanding to other industry verticals and geographies. Indicators and cyber risk insights obtained for those facilities contribute to a unique knowledge base.
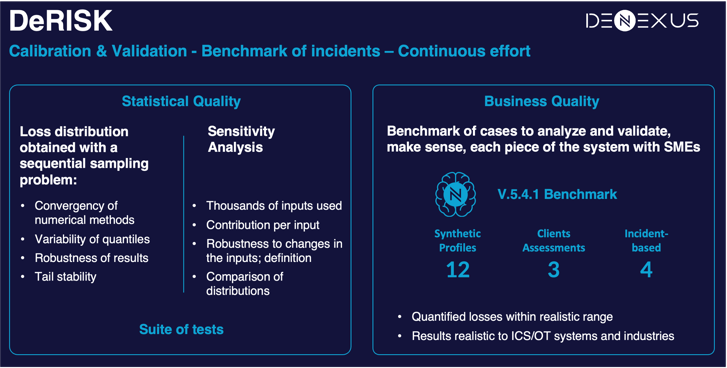
Industry benchmarks, enriched data, peer comparison, portfolios and risk accumulation analysis, definition and impact of mitigation projects, validation and calibration of modeling systems, and trends of cyber threat and losses are just a few of the use cases unlocked by the DeNexus Knowledge Center.
What is the DeNexus Knowledge Center?
The DeRISK Platform leverages data from +40 data sources that provide useful information for estimating losses due to cyber risk. This catalog of data sources comprises different leading solutions of telemetry from inside the installations, several of the main solutions that provide data on the cyber threat landscape and attack surface of the organizations, and the most important sources of information about vulnerabilities and disclosed cyber-attacks, among others.
The DeNexus Knowledge Center is the lodge of that information, all storage is in the DeNexus Trusted Ecosystem, a secure cloud-based infrastructure combination of data integrity, encryption and anonymization tools, security standards and certifications, trusted and certified infrastructure, policies and procedures that enables a strict control over the dissemination of data. With in-bound and out-bound dataflows, it is a knowledge base built with structured and non-structured data, from multiple open-source and multiple non-private or proprietary data curation engines.
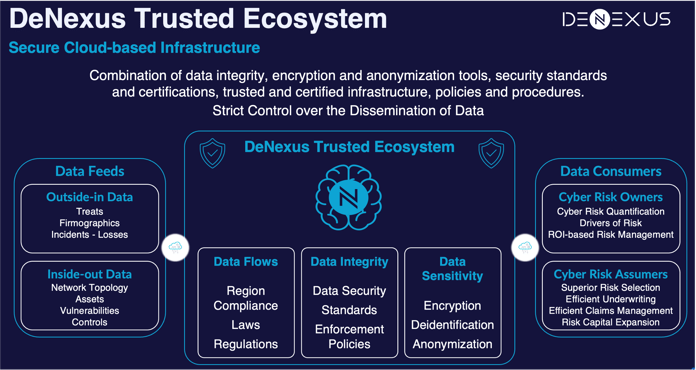
Types of Data
The DeNexus Knowledge Center holds data, indicators, and lessons learned from clients’ risk assessments, real cyber incidents, and portfolio analysis. The main types of data can be grouped into 5 categories: (1) Inside-out, (2) Outside-in, (3) Firmographics and Financial Loss Data, (4) Cyber incidents, (5) Risk assessments.
Inside-OUT data
Sensors in a company’s OT network automatically and continuously collect information about the assets, their connections, software, firmware, configuration, and information from the existing control systems. DeNexus has developed integrations with leading OT Asset Management and IDS (Intrusion Detection Systems) tools. The types of data used from inside-out sources are Asset inventory, Vulnerabilities by assets, Threat Detection, Security controls and their Maturity level (inferred indicator), etc. This data is stored in near real-time.
Outside-IN data
Data from public and private/proprietary sources is automatically collected and customized for the customer’s organization and its supply chain. The outside-in data is updated on a daily or weekly basis, depending on the source. The types of data used are:
- Threat monitoring: The number of credentials or email accounts found “in the wild”.
- Attack surface: Information on the client’s total external exposure footprint including the number of domains and subdomains, the number of public IP addresses, open ports, vulnerabilities per IP address, threat actors, leaked credentials, etc.
- Supply chain: Manufacturers, vendors, OEMs, directly or indirectly associated with the organization.
- Common Vulnerabilities and Exposures (CVEs) catalog vulnerabilities found, assessing their criticality in the context of each customer and installation from the Common Vulnerability Scoring System (CVSS) score and customer data (Outside-in and Inside-out), and assessing their exploitability from the Exploit Prediction Scoring System (EPSS).
- Unconventional signals from multiple external data sources (media mentions e.g., Twitter, popular news websites, etc.)
- Threat actor intelligence. Generation of threat actor intelligence from various external and internal sources to have the details of potential threat actors updated as needed.
- Detailed information from disclosed cyber incidents.
- Social monitoring sources are used to assess contextual information such as mentions of a company that can increase the attractiveness of a target company or sector
Firmographics and Financial Loss Data
Firmographics corresponds to specific organizational characteristics, including industry, reported revenues, and employee count, extracted from public data (or provided by the organization). Public operational and occupational risk datasets on the loss severity associated with different root causes combined with diverse public and proprietary databases on cyber incidents and losses to both quantify financial and nonfinancial impacts, identifying insurable and non-insurable impacts.
Financial loss data is challenging. Organizations are not compelled to explain how the incident occurred or how much money was lost because of it. Most commonly, they might even be required by law or regulations not to make that information public. This information is addressed by industry vertical.
Cyber Incidents Data
Although several alternatives exist for cyber incident data repositories, this type of information is scarce. While there are many observations in the databases, most variables are sparsely populated. This issue is compounded by the lack of relevant incident data, like security posture at the time of the incident. The DeNexus Knowledge Center contains information on cyber incidents from public databases. This information is obtained in two levels of aggregation:
- Single incidents data
- List of disclosed OT cyber incidents published by the OT community
- List of disclosed cyber incidents and data breaches published by the most relevant providers of repositories
- Aggregated incidents data
- Aggregated data on cyberattacks published by 3rd-party vendors on a regular basis – annually or semi-annually-. These reports – unstructured data – provide useful information such as the distribution of cyber incidents by region, industry, company size, etc.
Risk Assessments
As stated above, DeNexus has evidence-based inside data from operating assets in renewable power generation, that information combined with all other available data sources, in the DeNexus Knowledge Center we have insights on:
- Security Control Profiles per type of site with several frameworks
- ICS/OT Networks Risk Profiles based on the Inside-Out data
- Projects commonly built to mitigate risk
- Peers’ metrics on loss exposure, like expected loss in days of revenue.
- Scenarios to validate CRQ results
Click Here to read more about the DeNexus Knowledge Center and the DeNexus Trusted EcoSystem.
Click Here to learn more about DeRISK, a comprehensive Cyber Risk Quantification and Management platform!
