The Case for Measuring OT Cyber-Physical Risk.
A misconfigured PLC can generate downtime costs that exceed a refinery’s annual maintenance budget. Yet many plant managers still describe cyber exposure only as “high,” “medium,” or “low.” Few would manage a balance sheet with adjectives alone; cyber risk should be approached with the same level of discipline.
1. The OT Blind Spot
Operational technology (OT) governs furnaces, water pumps, cooling systems in data centers, runway lighting, electrical substations, and more—assets monitored in milliseconds and micro-amps. When assessing cyber risk, however, the discussion often reverts to qualitative heat maps or context-free scores.
This disconnect matters because:
-
- Downtime translates directly to lost revenue. A steel mill interrupted by ransomware can incur seven-figure losses per hour.
- Regulatory scrutiny is increasing. SEC cybersecurity rules, NERC CIP standards, the EU NIS 2 directive, U.S. TSA security directives, and others require demonstrable cyber-risk management.
- Insurance markets are tightening. Cyber and cyber-physical insurance are diverging. Underwriters now request quantitative evidence; without it, premiums rise or coverage may be withdrawn.
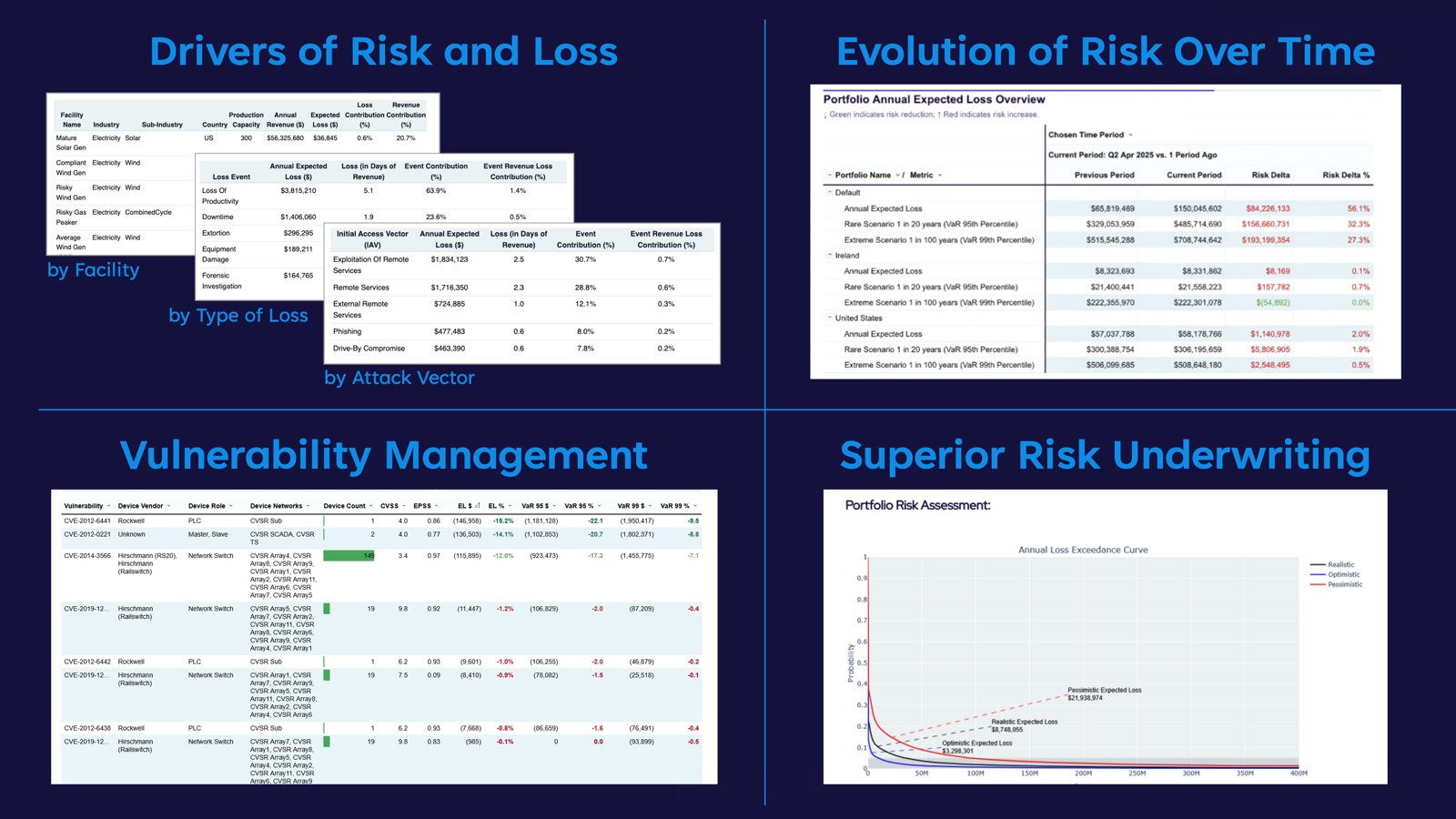
2. Financial Quantification of Cyber Risk Is Essential—and Requires OT Data
Financial quantification of cyber risk does not imply perfection. It is a systematic method for translating technical failure modes—such as a compromised SCADA system or a spoofed level sensor—into probabilistic, actuarial cash-flow impacts. Credible metrics rely on more than expert opinion or outside-in assessments; they require on-site OT network data that most facilities already collect:
-
- Asset inventory
- Vulnerability inventory
- Network topology
- Firewall rules
Without this information, estimates lack conviction, and the CFO is likely to discount any annualized-loss-expectancy (ALE) calculations.
3. A 4-Step Playbook to Quantify OT Cyber Risk
| Step | What You Do | What It Gives You |
| 1. Gather | Identify OT vulnerabilities, and gather network & firewall data. | Attack paths |
| 2. Prepare | Format the OT data listed above; clean, normalize, and ensure it correlates. | Evidence-based insight |
| 3. Calibrate | Combine expert input with OT data in Monte Carlo simulations (e.g., using DeNexus’ DeRISK). | A loss-probability curve |
| 4. Monetize & Iterate | Convert frequency × impact into ALE, then rerun after any significant process change. | Annualized Loss Expectancy, Value at Risk |
Tip: Begin with a single production site. The initial quantified result can serve as a template for other facilities.
4. Mitigation and Transfer - Two Levers, One Ledger
-
- Mitigation
Incorporate each control (e.g., remote access, anomaly detection, vulnerability management) into the model, rerun the simulations, and observe the projected loss reduction. OT data provides more accurate downtime savings projections, not assumptions. - Transfer
Underwriters respond favorably to reliable numbers. Underwriters like to see high maturity cybersecurity controls, as well as data-driven insights, as it makes their evaluation of risk easier while allowing the applicant to receive better limits, fewer exclusions, and lower premiums.
- Mitigation
5. From Spreadsheet to Boardroom
-
- Express results in financial terms, not merely in events, vulnerabilities, or cyber asset counts.
- Illustrate the 95th-percentile “worst day” (aka., potentially once in the next 20 years); executives remember clear scenarios.
- Update metrics monthly. The threat landscape and your environment evolve continually; timely data from inside your ICS/OT system correlated with timely threat intelligence preserves credibility.
6. The Takeaway
Industrial organizations have already mastered Six Sigma and predictive maintenance by collecting granular data and analyzing variance. Cyber risk warrants the same quantitative discipline. Measure it with internal OT network data to manage, mitigate, and transfer it effectively.
Call to Action
Select one critical OT asset. Spend an hour this week outlining its most serious cyber-failure scenario on paper. Then contact DeNexus. That outline is the first step toward a quantified risk model—and a more secure, cost-efficient operation.
If you found this useful, share it with a colleague who still labels risks as “medium” without consulting the historian.
If you want to learn more, get in touch with our team, or understand how the above is put to use to quantify and manage cyber risks at 250+ industrial sites monitored by DeNexus, you can contact us at https://www.denexus.io/contact.