In today's complex cybersecurity landscape, traditional vulnerability management falls short. Many organizations still rely on severity and exploitability scores to prioritize vulnerabilities, often overlooking the broader risk context. That context is provided by DeRISK Quantified Vulnerability Management -DeRISK QVM-, a smarter approach that integrates DeNexus’ flagship DeRISK Cyber Risk Quantification -DeRISK CRQ- to drive more effective decision-making. DeRISK QVM takes risk-based vulnerability management to the next level by leveraging digital twin simulation with DeNexus cyber risk models, transforming how businesses manage cyber risk.
The Limitations of Traditional Vulnerability Management
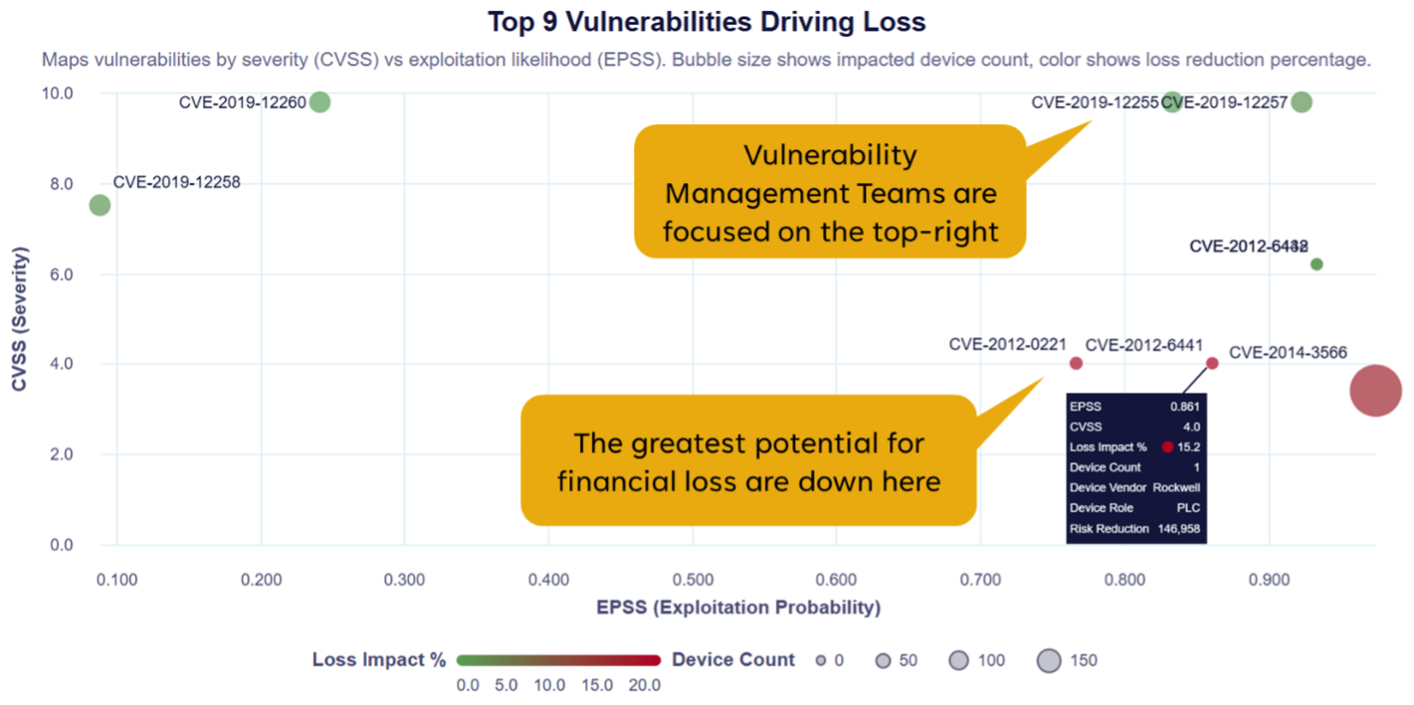
Conventional vulnerability management strategies typically prioritize security gaps based on severity ratings from the Common Vulnerability Scoring System (CVSS), exploitability predictions from the Exploit Prediction Scoring System (EPSS), and US DHS CISA’s Known Exploited Vulnerabilities (KEV). While these frameworks provide useful insights, they fail to account for an organization's unique risk landscape. Not all vulnerabilities present the same level of risk—some may have high CVSS severity but exist in isolated environments, while others with lower scores may be critical within an attack path. Without considering how vulnerabilities contribute to a full attack chain, organizations may misallocate resources on patches or implementations of controls that don’t drive the most effective reduction of risk.
Why Understanding the Attack Path Matters
Cyberattacks rarely occur in isolation; they follow complex, multi-step paths to compromise systems. Some vulnerabilities serve as steppingstones, significantly amplifying an attacker's ability to move laterally and escalate privileges. DeRISK QVM acknowledges this reality, prioritizing vulnerabilities not just on severity, but on their role within an attack path contextualized with the presence (or lack) of cybersecurity controls. This ensures that organizations address the most strategically important weaknesses first, reducing the likelihood of high-impact breaches. 

The Role of Cyber Risk Modeling in Quantified Vulnerability Management
DeRISK QVM introduces an innovative approach by incorporating cyber risk modeling through, a powerful technology that creates a virtual representation of an organization’s ICS/OT cyber environment. This enables security teams to model various attack scenarios and understand the financial repercussions of different vulnerabilities. Rather than guessing at potential losses, companies can leverage data-driven insights to quantify cyber risk in real financial terms.
With DeRISK QVM and DeRISK CRQ, organizations can move beyond theoretical scores and test real-world risk-based vulnerability management strategies. By simulating various defensive actions, companies can identify the most cost-effective approaches to reduce cyber risk. For example, mitigating the top riskiest N vulnerabilities, how much does this reduce the overall financial risk across an organization?
-2.png?width=612&height=434&name=image%20(1)-2.png)
This risk-driven, data-driven approach enables organizations to make informed security decisions based on measurable financial benefits rather than arbitrary prioritization.
The Business Case for Quantified Vulnerability Management (QVM)
DeRISK QVM does more than just enhancing cybersecurity. It strengthens business resilience and justifies security investments. By quantifying cyber risk in financial terms, security leaders can effectively communicate the value of mitigation efforts to executive teams. This helps organizations allocate resources wisely, ensuring cybersecurity budgets deliver the maximum reduction of financial loss potential.
DeRISK enables organizations to shift from reactive security measures to a proactive risk management strategy grounded in financial insight. By leveraging advanced analytics and modeling techniques, businesses can prioritize their security efforts based on actual risk reduction rather than theoretical severity scores. This approach not only improves cyber resilience but also aligns cybersecurity initiatives with broader business objectives, ensuring long-term operational stability.
Ready to add financial quantification of risk to your vulnerability management approach? Discover how DeRISK can transform your cybersecurity strategy today.
If you want to learn more, get in touch with our team, or understand how the above is put to use to quantify and manage cyber risks at 250+ industrial sites monitored by DeNexus, you can contact us at https://www.denexus.io/contact.