Data Centers can’t afford generic patch lists. In OT environments—where downtime hits revenue and safety—risk-based vulnerability management outperforms CVSS & EPSS-only sorting. This guide explains how DeRisk Quantified Vulnerability Management (QVM) helps CISOs and OT security leaders prioritize by business impact, not just technical severity.
The Problem with CVE Lists in OT
- Maintenance windows are scarce and patching can disrupt production, or not be available at all.
- A “critical” score doesn’t reflect exploit likelihood, asset criticality or business criticality.
- Teams waste time on low-impact issues while high-risk exposures persist.
What “Risk-Based” Actually Means
Risk = likelihood × impact. For vulnerabilities, that means blending:
- Exploit likelihood (e.g., CVSS, EPSS, threat intel, active exploits)
- Asset criticality (process importance, safety, revenue)
- Exposure/attack path (network reachability, cybersecurity controls)
- Business impact (modeled financial loss if exploited)
How DeRISKTM QVM Works (Step-by-Step)
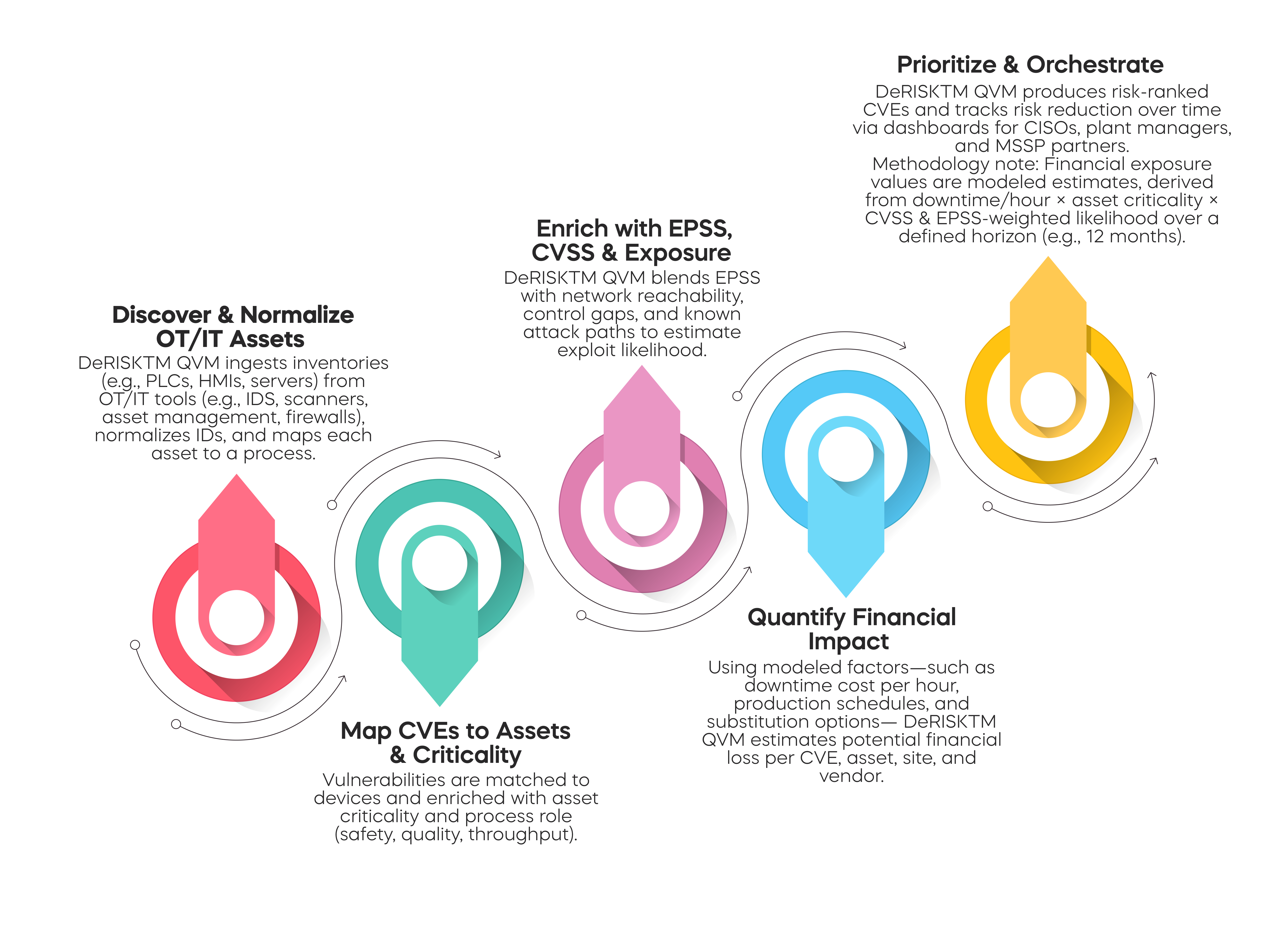
Data Centers Use Case
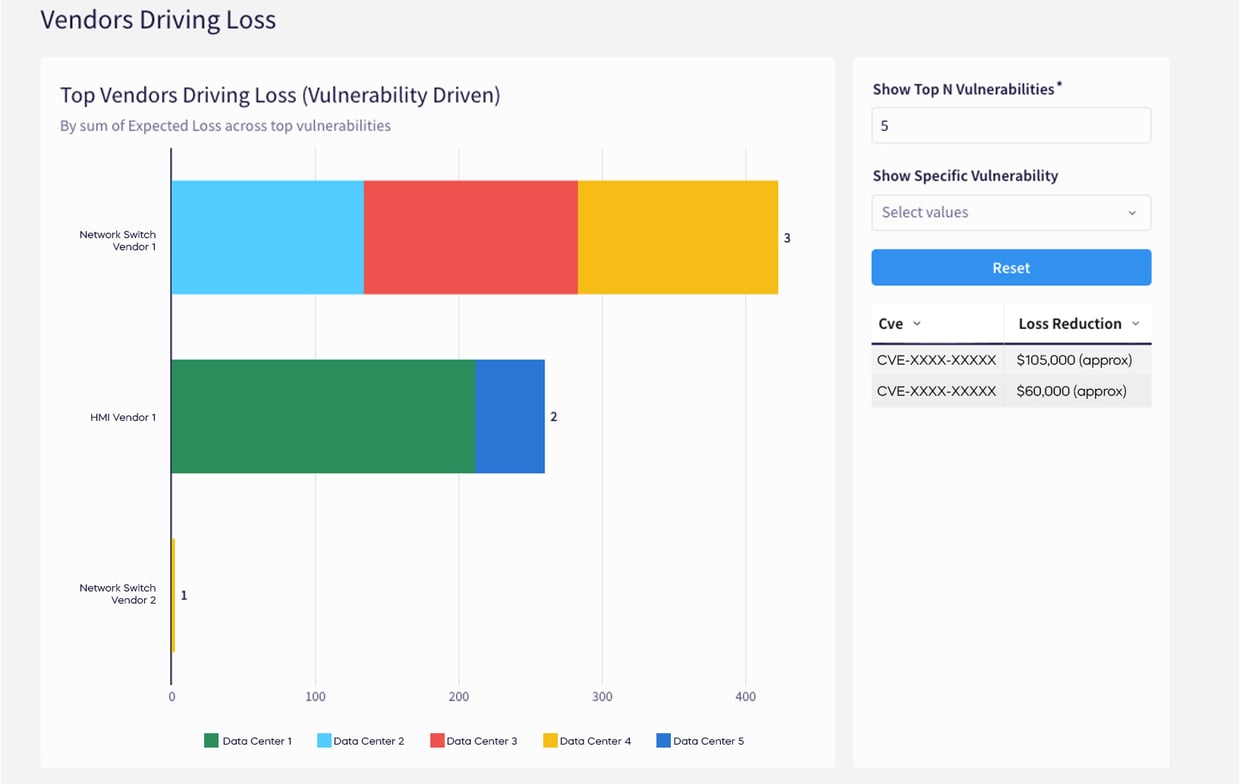
A leading global hyperscale data center operator conducted assessments across its global sites. Instead of relying solely on CVSS and EPSS rankings, DeRISK™ QVM pinpointed the vulnerabilities with the highest financial impact, helping teams focus limited maintenance windows on the most critical fixes.
Example Findings (anonymized)
|
CVE |
Exposed Devices |
EPSS (est.) |
Total Annual Loss Reduction |
|
CVE-XXXX-XXXXX |
300 |
0.03 |
$105,000 (approx) |
|
CVE-XXXX-XXXX |
200 |
0.03 |
$60,000 (approx) |
Before/After
Before: Long CVE list by severity; little clarity on business impact.
After: Vulnerability insights (Across all Data centers):
- Total CVEs: 4,500 (approx)
- Distinct CVEs: 20
- Risky CVEs: 3
- 0 in CISA KEV catalog
- Risky / Distinct: 10.0%
- Top 5 CVEs : Drive 100.0% of overall risk
- Top 5 CVEs Present in 3 facilities
- 0 in CISA KEV catalog
- Top 5 as % of distinct CVEs: 10.0%
- Riskiest Data Centers: Two data centers located in the EU
- Riskiest Devices: Network Switch Vendor 1 and HMI Vendor 1
CVSS vs EPSS vs Risk-Based: What to Use When
|
Approach |
What It Does |
Useful When |
Limits in OT |
|
CVSS |
Technical severity based on base metrics |
Quick triage, compliance baselines |
Ignores exploit likelihood & business impact |
|
EPSS |
Probability a CVE will be exploited |
Threat-led prioritization |
Doesn’t include asset criticality or cost |
|
Risk-Based (QVM) |
Combines likelihood + impact (financial) enabling risk-based vulnerability management |
Maintenance-constrained OT, board reporting |
Requires data inputs & modeling assumptions |
Outcomes & KPIs to Track
- Risk reduced ($): delta in modeled exposure post-remediation
- High-risk exposure reduction: % of top-decile items addressed
- Mean time to remediate (MTT-R): prioritized items only
- Actions without patch: % risk reduced via compensating controls
- Time-to-decision: from detection → scheduled change
Implementation Considerations in OT
- Maintenance windows: Coordinate with production; batch changes.
- Vendor constraints: Respect warranties; use vendor-approved mitigations.
- Compensating controls: Network segmentation, allowlists, monitoring.
- Safety & quality: Align with plant SOPs and change control.
Ready to align remediation with business impact? Click here book a DeRISKTM QVM demo and see DeRISKTM QVM in action.

FAQs
- What is risk-based vulnerability management?
- EPSS vs CVSS—what’s the difference?
- How do I prioritize CVEs when patching is hard in OT?
- How do you quantify the business impact of a CVE?
- What metrics should CISOs track?
