Diagram showing how cyberattacks move from IT networks into operational technology environments
Key Takeaways
What OT Leaders Need to Know from DSIT's 2025 Study:
- Ransomware is the #1 disruptive threat to UK Critical National Infrastructure, with attacks frequently starting in IT systems before pivoting into OT environments
- Legacy OT systems (30-50 years old) represent the most significant OT-specific vulnerability, as they cannot be patched and were never designed for today's connected threat landscape
- Critical skills shortage in OT cybersecurity is constraining organizational capability more than budget limitations
- Weak IT/OT segmentation enables lateral movement from enterprise networks into industrial control systems
- Third-party and supply chain risks amplify exposure through hard-to-assess vendor security and remote access practices
- Cyber Risk Quantification (CRQ) provides the "missing decision layer" to translate security findings into board-ready, financially articulated choices
In the UK Department for Science, Innovation and Technology (DSIT) Operational Technology Cyber Security Study titled "Researching the cyber security vulnerabilities of Operational Technologies and the risks they pose" published on December 23, 2025, Arcanum Information Security's Project Lead Jane Chappell sets out a clear premise: DSIT commissioned the work to "comprehensively research the cyber security risks posed to Operational Technologies (OT) in both critical and non-critical national infrastructure" and to inform UK policy and resilience improvements.
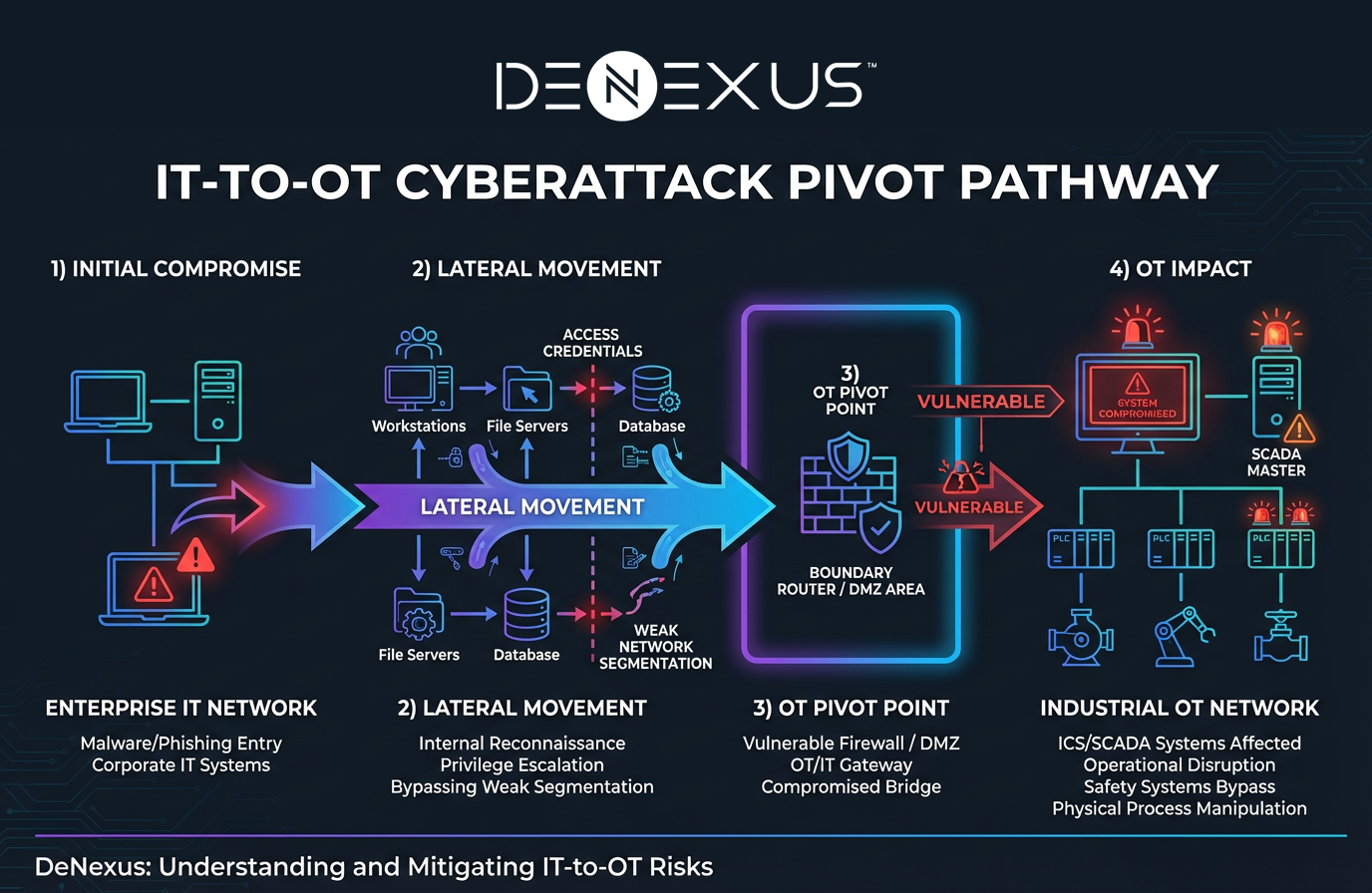
For OT leaders, the report's implications are practical: ransomware is treated as the most immediate disruptive threat to Critical National Infrastructure (CNI), nation-state activity is persistent, and—critically—OT compromise frequently starts with IT compromise, then pivots "beneath" into control environments.
Key Findings from the DSIT OT Security Study
Methodology and Scope
The study triangulated DSIT-approved qualitative interviews (25 interviews covering 30 individuals across almost all UK CNI sectors plus manufacturing/engineering) with a literature review of 160+ sources (128 used), supplemented by an expert questionnaire (7 responses), and analyzed interview transcripts using qualitative content analysis. It focused on OT technology/process risks (explicitly excluding human factors/social behavioral aspects).
Recurring Themes in OT Security
The most recurring themes identified in the study were the security impact of legacy OT systems, the role and effectiveness of legislation and regulation, and the need for increased government support and cross-sector knowledge sharing. Skills pipeline decline, third-party and supply chain security, attack vectors, boardroom understanding, and foundational practices like asset registers and incident management also emerged strongly.
OT Threat Landscape: Nation-State vs. Ransomware
The report distinguishes CNI threats as primarily nation-state or state-sponsored (where service disruption can have debilitating national effects) versus non-CNI threats as predominantly financially motivated cybercrime—especially ransomware—because operational disruption creates leverage to pay. It also underscores that attacks frequently begin via enterprise IT access and then pivot into OT, reflecting the practical reality of IT/OT interconnectedness.
Common OT Vulnerabilities and Mitigations
The most significant recurring vulnerabilities include weak IT/OT segmentation (enabling lateral movement), poor asset visibility (including "in-between" boundary infrastructure being unmanaged), and exposure through remote access and removable media practices. The most emphasized mitigations are defense-in-depth controls—stronger segmentation (DMZ/iDMZ and micro-segmentation where needed), risk-driven remote access design, and robust role-based and physical access controls—implemented in ways that minimize operational disruption.
The Legacy OT Challenge
Legacy OT increases risk because older systems often cannot be upgraded or patched, may lose "air gap" protections over time, and were not designed for today's connected threat environment; yet replacement is frequently constrained by cost and downtime impacts. As a result, organizations commonly treat legacy as a "necessary evil" and focus on compensating controls and defense-in-depth around the assets, revisited through ongoing risk-informed review.
Skills Pipeline and Workforce Retention Crisis
A key finding is a critical shortage of professionals with combined OT and IT expertise, with interviewees describing an insufficient resource pool and a weak pipeline as experienced practitioners retire. The report links improvement to better availability of OT security knowledge and more practical, hands-on pathways and outreach to develop and retain OT-capable cyber skills.
Third-Party and Supply Chain Risks
Third parties are repeatedly identified as a risk amplifier—through hard-to-assess supplier security, complex multi-party delivery models, and especially vendor remote access and cloud-enabled services that can expose OT without adequate customer control or visibility. Stronger procurement discipline (pre-contract checks, explicit security requirements/liability and audit rights) and adoption of clearer minimum supplier standards are highlighted as key levers, noting that many UK businesses still set few minimum supplier security requirements.
The IT-OT Divide
Differing priorities (IT: confidentiality/integrity; OT: safety/availability) and distinct cultures and lifecycles have slowed OT security adoption and complicated convergence—even as interconnectivity expands the attack surface and introduces new vulnerabilities. The divide can also create "gaps in ownership," leaving boundary components (e.g., routers/switches linking OT to enterprise IT) ignored by both sides and therefore unpatched and unmonitored.
Security Governance and Board Engagement
The report frames security governance as clear authority and accountability for security decisions, enabling informed risk management aligned to business objectives, with regulation (e.g., NIS Regulations and the NCSC Cyber Assessment Framework) shaping expectations for "appropriate" and evolving controls. Interview evidence shows mixed board-level engagement, and warns that weak governance and unclear roles/responsibilities lead to poor risk management and underinvestment in OT security fundamentals.
Legacy OT Challenges vs. Risk Quantification Solutions
|
Legacy OT Challenge |
Risk Quantification Solution |
|
Cannot patch 30-50 year old systems |
Quantify Annual Loss Exposure (ALE) of leaving legacy assets in place vs. compensating controls |
|
Fear of disruption from active scanning |
Model risk reduction from passive monitoring and segmentation alternatives |
|
Unclear ROI for replacement |
Calculate Annual Loss Exposure (ALE) vs. remediation investment with scenario analysis |
|
Limited budget justification |
Express risk in financial terms boards understand (expected losses, worst-case scenarios) |
|
Competing IT vs. OT priorities |
Provide shared language (monetary impact) for IT, OT, finance, and operations teams |
|
Skills shortage constraints |
Prioritize work by marginal risk reduction per unit of scarce resource |
Why Cyber Risk Quantification Matters for OT Security
The DSIT Operational Technology Cyber Security Study is fundamentally a call for risk-informed decision-making in environments where the consequence of compromise is not just data loss, but real-world safety, availability, and cascading service disruption. It highlights how OT compromise is frequently enabled through IT access paths, how legacy OT persists because replacement is operationally and financially prohibitive, and how governance, supply chain management, and scarce OT-security skills constrain what organizations can realistically do at scale.
This is exactly where Cyber Risk Quantification (CRQ) strengthens the report's recommendations. UK government guidance explicitly introduces cyber security risk quantification as a way to express cyber risk using measurable metrics (including financial cost) to support better decisions. In parallel, NIST's IR 8286 series frames cybersecurity risk management as an enterprise risk discipline—emphasizing prioritization, response selection, and communication of cybersecurity risk in ways that leaders can act on (including quantifying organizational impact and consequences). Quantitative methods such as FAIR (Factor Analysis of Information Risk) are specifically designed to analyze and quantify cyber/operational risk in financial terms, giving executives a common unit of measure for comparing scenarios and investments.
Quantifying the "Unpatchable" Legacy Problem
Across the report's subjects, CRQ is the missing "decision layer" that translates good security practice into board-ready choices. For example, the report repeatedly surfaces challenges like legacy equipment that cannot be patched, fear of disruption from active scanning, and the practical reliance on defense-in-depth compensating controls rather than wholesale replacement.
CRQ complements this by quantifying (a) the expected annual loss exposure (ALE) of leaving a legacy asset in place, (b) the risk reduction achieved by segmentation, access control hardening, monitoring, or recovery improvements, and (c) the economic trade-offs of downtime versus remediation—turning "we can't patch it" into a defensible, monitored, financially articulated risk acceptance decision.
Optimizing Scarce Resources with Risk-Based Prioritization
Similarly, the report's themes on the skills pipeline and the IT–OT divide implicitly point to a resourcing problem: even with budget, capability is limited, and priorities must be brutally clear.
CRQ helps here by ranking work by marginal risk reduction per unit of effort and spend, and by providing a shared language for IT, OT, finance, and operations—reducing "OT safety vs IT security" debates into quantified business outcomes.
Building a Risk-Based Vulnerability Management Program for OT
Flowchart showing how cyber risk quantification supports OT security decisions
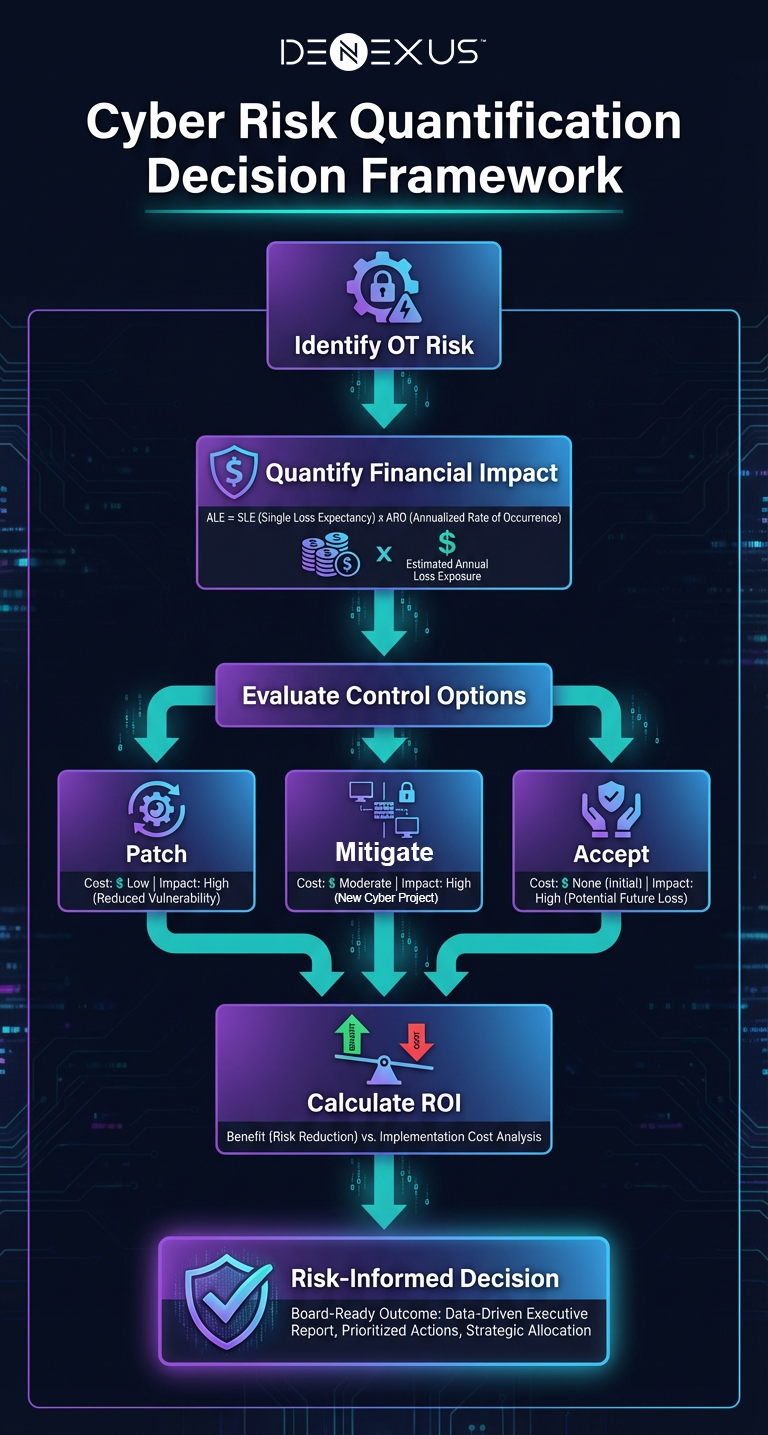
OT-specific cyber risk quantification enables a risk-based vulnerability management program by answering, for each vulnerability (or exposure condition), a business question: "If this is exploited in our OT environment, what is the expected loss (and worst-case loss), and how does remediation compare to compensating control options?"
Practically, a quantified vulnerability management (QVM) model for OT should:
- Tie vulnerabilities to OT assets and process criticality (including safety and shutdown constraints)
- Incorporate realistic exploit paths (IT-to-OT pivot, remote access, between network zones, between cyber assets)
- Account for control strength and detectability (especially where scanning is constrained)
- Produce a ranked remediation plan based on quantified risk reduction per unit effort—so maintenance windows and engineering outages are spent where they reduce risk the most
Solutions like DeNexus' Quantified Vulnerability Management (QVM) translate vulnerabilities and controls into financial risk metrics (dollars at risk) and enable prioritization of remediation based on business impact rather than CVE severity—exactly the risk-informed approach the DSIT study advocates.
Operationalizing DSIT's Recommendations with Quantified Risk
For organizations using the DSIT report as a roadmap, the challenge is translating its findings into defensible, actionable decisions at both strategic (board, investment, supplier selection) and tactical (patch prioritization, control design, incident response) levels.
Tools such as DeNexus' Cyber Risk Quantification (CRQ) platform quantify cyber risk in monetary terms for industrial and OT environments, leveraging both internal ("inside-out") and external ("outside-in") data with sector-specific modeling to support governance and investment decisions. This approach provides the quantification and scenario analysis needed to justify segmentation, resilience investments, and other cyber mitigations—while enabling continuous, risk-based vulnerability management that is credible to both OT engineers and boards.
Conclusion: From Research to Risk-Informed Action
The DSIT 2025 OT security study provides comprehensive evidence of the vulnerabilities, threats, and systemic challenges facing UK operational technology environments. Its value lies not just in identifying problems, but in establishing a foundation for risk-informed, proportionate response.
By integrating cyber risk quantification into OT security programs, organizations can move beyond compliance-driven checklists to truly risk-based decision-making—prioritizing investments where they reduce the most financial exposure, articulating legacy risk in terms boards understand, and building vulnerability management programs that align with operational realities and resource constraints.
For OT security leaders navigating the complex landscape described in the DSIT report, quantified risk management transforms good intentions into measurable, defensible action.
Download the Full DSIT Report:
Learn More:
