Understanding the maturity level of your cybersecurity controls is key to ensuring robust cyber defenses. The maturity model you choose—and how rigorously you adhere to it—can significantly influence your organization's security posture. It’s also common for large organizations to employ a combination of standard and custom-developed models. Below is an overview of some prevalent cybersecurity maturity models and their unique features:
- NIST Cybersecurity Framework: A widely used framework from the U.S. National Institute of Standards and Technology (NIST), offering a comprehensive collection of cybersecurity best practices and guidelines. The NIST CSF establishes implementation tiers, that focus on risk management, the program, and external participation. Other maturity models focus on processes, whereas NIST CSF tiers focus specifically on risk management only.
- C2M2 MIL: Developed by the Department of Energy, this model is tailored for Energy sectors but also suits a variety of organizations managing IT and OT assets. The acronym MIL refers to Maturity Indicator Levels, which range from 0 to 3. C2M2 is unique in that it specifies security controls required to achieve different maturity indicator levels.
- DoD CMMC: Designed to meet the U.S. Department of Defense's security requirements of third-party contractors/suppliers, but the Cybersecurity Maturity Model Certification (CMMC) has been applied for broader applications across other industries.
- IEC 62443-2-4: Maintained by EIC (International Electrotechnical Commission), this standard establishes requirements for third-party ICS/OT service providers into maturity levels.
- CMMI: Originally developed by CMU (Carnegie Mellon University) in the 90s, the most widely adopted CMMI version 1.3 is still publicly available. This standard focuses on ensuring that business processes are capable of achieving their mission with predictable outcomes. It is now maintained by the CMMI Institute of ISACA.
Maturity in cybersecurity controls is not just about having measures in place; it's about the effectiveness and certainty of those controls and whether your processes are reactive or proactively designed. Cyber security controls can range from ad-hoc to pre-planned or proactive processes. It’s important to note that they can both get the job done. The difference is the speed, efficiency, scale, and assurance that the task gets done systematically, including times of stress (like an attack or facility outage) and by different people. Planning and measurement is at the core of maturity. Consider these questions:
- When did you last strategize against ransomware?
- How might a ransomware attack breach your defenses?
- What impact could a cyberattack have on your data and backup systems?
- Do you have an incident response plan in place for cyber incidents? Who is trained on the plan?
Proactive planning for scenarios like ransomware attacks ensures that your business remains resilient, minimizing disruption and facilitating a swift recovery.
Let’s look at the specifics of cyber security maturity for industrial facilities, operational infrastructure, or OT networks.
|
Maturity levels |
Representative characteristics |
|
Low Maturity |
|
|
Medium Maturity |
|
|
Advanced Maturity |
|
Attaining advanced cybersecurity maturity necessitates a strategic planning mindset and disciplined execution to relentlessly, step-by-step implement required controls that achieve predictable resilience in the face of adversity.
Why Improve Cybersecurity Maturity?
A primary reason for attaining higher maturity levels is that well-implemented and maintained processes, tasks, and security controls significantly increase the likelihood of successfully preventing attacks. For example, as detection or response processes become more mature, the probability of detecting an attack in its early stages gets higher, enabling teams to more rapidly contain the incident. The net effect is that mature detection and response will reduce the severity of impact, ultimately reducing the financial losses associated with a cyber event.
For cybersecurity frameworks like NIST CSF, ISO 27001, and the DeNexus Cybersecurity Framework, we rely on maturity level as a measure of effectiveness and probability that the security control will fulfill its objective. This is different than the binary compliance view of cybersecurity, which is either Compliant or Non-Compliant. Yes, a low-maturity security program can be compliant. The only certainty is that the regulatory requirements are fulfilled. However, in times of stress, such as an actual cyber-attack, the maturity level of a process or security control increases the probability that it will protect/detect/recover.
In DeRISK, the maturity level of each security control is used as a model input that affects the attack paths, probability of impact, as well as the financial losses of an event.
DeNexus: Enhancing Maturity Visibility
DeNexus streamlines the process of aligning with various cybersecurity standards and frameworks. For example, our DeRISK platform visualizes an organization's adherence to the 108 controls of the NIST CSF and facilitates tracking and benchmarking against industry peers. By addressing lacking controls, organizations can proactively shore up their cyber security defenses and mitigate future risks. DeNexus also provides a benchmark against industry peers so that every facility and asset owners can benefit from comparison with other facilities.
The figure below illustrates one of the many comparisons available within DeRISK (in this case as at an aggregated level with comparison to industry peers).
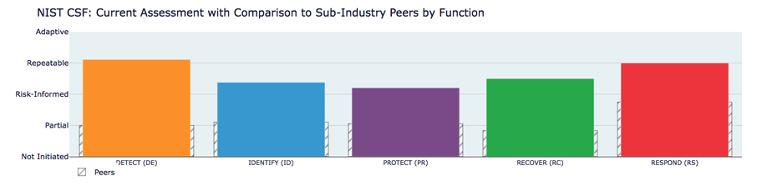
By addressing lacking controls, organizations can proactively shore up their cyber security defenses and mitigate future risks. Complementary access to DeNexus is now available to energy companies. Contact us and ask for more information or a free trial.
A Prognostic Indicator of Cyber Risk
Ask cybersecurity staff how overworked they are, or how much of the important projects they have to constantly defer. Somewhere in there, projects or tasks are being dropped, cracks in cyber security posture are widening, and opportunities for damaging cyber events are rising.
