Navigating the complex labyrinth of securing IoT and OT systems in an expanding attack surface for cloud data centers requires a delicate balance of innovation, standards and quality for Cyber Risk Quantification and Management across multi-data center ecosystems.
The evolution of advanced technologies like Artificial Intelligence (AI) and edge computing is catalyzing an unprecedented demand for data centers. These technologies require enormous computational power and data storage capabilities, contributing to the expansion of data center ecosystems worldwide.
Add the ongoing wave of mergers and acquisitions, and it's clear that today's corporate landscape is experiencing an unparalleled flux in technology infrastructure. Furthermore, global sustainability requirements are pushing the envelope for innovation, compelling data centers to embrace greener technologies.

In this intricate web, Building Management Systems (BMS) and Data Center Infrastructure Management (DCIM) systems emerge as risk areas with an intricate, constantly evolving asset profile, intensifying the challenge of securing an ever-expanding attack surface.

Standards such as TIA-942, ASHRAE, and the Uptime Institute have helped guide Data Center owners in areas of redundancy and resiliency, but these standards lack an emphasis on cyber security elements for increasingly interconnected IT, IoT (Internet of Things), and OT (operations technology) systems. This gap in focus amplifies the need for securing a rapidly expanding attack surface of critical assets, where new technologies providing the following challenges related to security:
- Asset visibility is difficult to acquire through monitoring solutions across different OT networks.
- Prioritization of physical security due to a high level of vendor interaction with the different technologies.
- Asset criticality is inconsistently measured without understanding the business impacts associated with loss of function or misuse.
Harmonizing Security Standards and Asset Complexity is a Multidimensional Challenge in Data Center Management. Each industry standard serves as a unique lens, focusing on different elements of data center infrastructure—from TIA-942's emphasis on electrical systems and safety to Uptime Institute's layered approach to capacity and redundancy, and ASHRAE's meticulous guidelines on climate control.
Challenges arise in effectively monitoring these controllers, especially when they use specialized protocols like BACnet, necessitating the need for specialized OT cybersecurity solutions that can conduct both passive and active monitoring without inadvertently compromising system integrity.
As organizations attempt to comply with these diverse sets of rules, they invariably introduce a complex mix of vendors, equipment, and technologies into their environments. This array might include Programmable Logic Controllers (PLCs) for automation, an assortment of switches and controllers for network management, and a variety of IoT devices like temperature and humidity sensors for environmental monitoring.
Additionally, access control system security is an essential pillar in safeguarding data center environments, serving to regulate both physical and digital access to critical resources. These systems often employ multi-layered authentication mechanisms, such as smart cards, biometrics, and PIN codes, to ensure that only authorized personnel can access sensitive areas or systems within the facility.
On the network level, advanced firewalls and segmentation rules help restrict the communication of critical system controllers—such as those for fire suppression systems—to authorized endpoints only.
Addressing various security elements at the same time can go awry in several ways—underinvestment in security controls for seemingly less-important assets, misaligned priorities that don't reflect the real-world importance of specific systems, or inadequate monitoring solutions that can't provide a holistic view of asset health.
In other words, while the physical and cyber safeguards may be sophisticated on their own, their true efficacy can only be gauged when seen through the lens of financial business impact.
Failure to assess the criticality of each asset—from fire suppression system controllers to badge readers—within the broader context of organizational goals and risk tolerance can result in vulnerabilities that are not apparent until a security incident occurs. Therefore, asset criticality should be consistently measured and periodically reviewed, integrating insights from facility managers, cybersecurity teams, and business leaders to ensure a well-rounded, business-centric security posture.
Efficiently managing the attack surface is complex. Organizations should look to sophisticated solutions like DeNexus’ DeRISK Cyber Risk Quantification & Management (CRQM) platform. DeRISK starts by aggregating key cybersecurity evidence-data from both Inside-Out and Outside-In data sources. Using frameworks such as NIST CSF, ISO 27001, and DeNexus’ proprietary DNX CSF (DeNexus Cybersecurity Framework), integrating these metrics seamlessly with data from different passive OT monitoring.
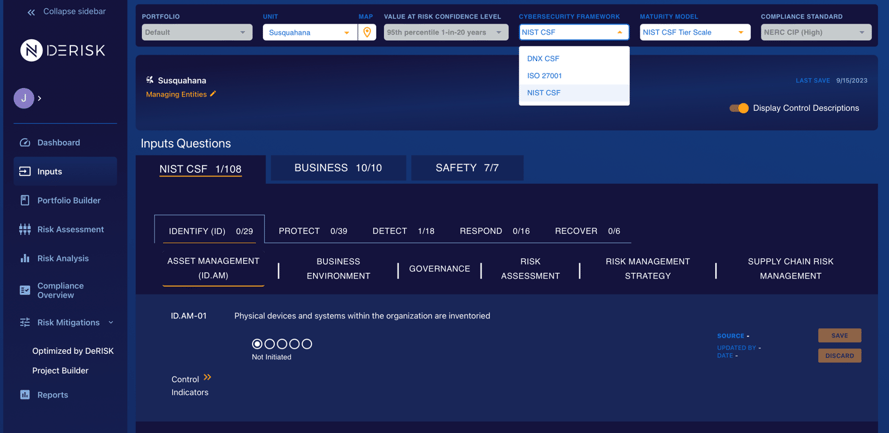
DeRISK enriches this integrated dataset by incorporating business operational metrics specific to data centers—such as energy consumption rates, system availability percentages, and cooling efficiency ratios. These metrics enable organizations to derive more nuanced insights into their overall risk profile, combining the typically siloed worlds of Cybersecurity and Operational Technology. By synthesizing all of this data, the DeRISK translates multifaceted insights into quantifiable business impact, thus allowing for well-informed, strategic decision-making facilitated by DeRISK Cyber Project Simulator that aligns with both organizational goals and risk tolerance. This holistic approach provides an enhanced security posture that meets the high standards of multiple leading industry guidelines.
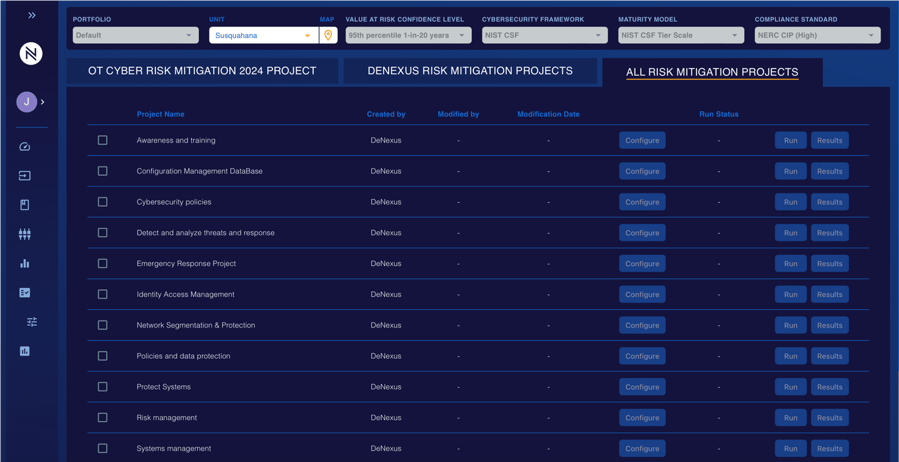
In conclusion, DeNexus has recognized the mass migration from on-premise IT infrastructure (e.g., email, applications, storage) to the Cloud. We anticipate that datacenter demand will grow at incredible rates. Also, as a shared, critical infrastructure to thousands of companies we see the need for Cyber Risk Quantification and Management growing for data centers to help them manage the cybersecurity risks of their OT infrastructures.
